What is Smishing?

Table of Contents
The Definition of Smishing
Smishing is a type of phishing that uses SMS messages to deliver malicious links and to trick and exploit people into performing a task that benefits a cybercriminal. Increasingly, other mobile messaging platforms are also being hijacked by nefarious entities. Smishing is sometimes called SMS phishing or mobile phishing. Smishing is increasingly popular as a way to steal sensitive and personal data as well as financially exploit individuals and businesses.
Organizations worldwide have embraced mobile devices, with 82% of businesses having a BYOD (Bring Your Own Device) program. The ubiquitous use of smartphones at work is one of the reasons why cybercriminals target our mobile devices by using smishing.
Here we look at what smishing is, why it is so successful, and how to prevent becoming a victim of phishing.
What is Smishing?

Smishing is an ideal way to initiate or deliver a cyberattack, as text messages have an open rate of 98%. New channels are being added to the umbrella term smishing, which can also include messaging apps like WhatsApp, Telegram, etc.
Smishing attacks are used to do something that benefits a cybercriminal. This could be revealing corporate data or login credentials or releasing monies. Credential theft can quickly lead to ransomware or other malware infections.
While most people understand email phishing, smishing is less known. A survey found that only 30% of respondents knew what smishing was. This is problematic, as ensuring that employees are security aware is a core measure to prevent cyberattacks on organizations.
Research has shown that roughly 28% of phishing attacks are due to smishing, with a further 24% focusing on messaging apps. These smishing campaigns often target login credentials, with 40% of mobile device-based threats attempting to steal credentials.
Cybercriminals are increasingly focusing phishing campaigns on mobile devices. The image below shows the phishing entry points initiated on a mobile device. The overlap between phishing and mobile devices has made it challenging for users to identify smishing attempts, as mobile numbers may display a spoofed brand name that is trusted and familiar.
Mobile Phishing "Mishing" Entry Points in 2024
Source: Zimperium
What Happens if Your Business is a Victim of a Smishing Attack?

Smishing attacks may be targeted or sent in a mass attack. Attackers identify target phone numbers either by obtaining them from previous data breaches or by gathering intelligence on a target. The resulting smishing attack is designed to manipulate the recipient of the malicious message in an attempt to extract something that benefits the attacker.
Typical outcomes of a smishing attack include stolen login credentials, personal information that can provide details needed to carry out further cyberattacks, or financial theft. Exploiting these data can lead to widespread business disruption, including loss of productivity and substantial and costly downtime.
Cyberattacks against a business may be multi-part, and smishing may be just one part of a longer attack chain that leads to substantial data or financial losses. Business Email Compromise (BEC) is an example of a longer attack chain that could be initiated by a smishing message. BEC attacks rely on gathering corporate intelligence and may involve the compromise of a CEO or CFO email account. A smishing message could be used to steal login credentials or gather data on a target. A smishing message could also potentially result in a wider network ransomware infection if login credentials are stolen.
The Cost of Smishing
Smishing is used to initiate a longer chain of security exploits or directly steal data and/or money. Like phishing, smishing leads to data breaches, ransomware infection, and Business Email Compromise (BEC). These costs of each have been estimated as follows:
Data breaches: The average cost of a data breach in 2024 was $4.88 million.
Ransomware infection: The average cost of a ransomware infection mitigation is $1.85 million
Business Email Compromise: The average cost of a successful BEC scam is $137,000
Why Does Smishing Work?
Like other forms of phishing, smishing heavily utilizes social engineering, with tactics that rely on manipulating human behavior. A smishing attack aims to encourage certain actions, such as clicking on a link in an SMS text message or replying to the text. Social engineering tactics to motivate these actions include manipulating employees using:
Trust
Cybercriminals will compose SMS text messages that engender trust. Because of how SMS services work, attackers can make a text message look like it has come from a trusted brand.
Personalization
A smishing campaign may target an individual employee or business. In this case, the scammers will have gathered intelligence on the employee or company to create an SMS text that uses personal details. Personalization helps to build a connection with the victim.
Urgency
The smishing message may use language that encourages a sense of urgency, such as "a security breach has occurred, and the victim must log in to a corporate app account to change a password".
Seven Common Types of Smishing Attacks
Smishing messages carry various scams and initiate more complex cyberattacks. Below are some of the most common forms of smishing; however, it is important to note that cybercriminals continuously change their tactics to evade detection.
#1: Delivery Smishing
A favorite form of smishing is the spoof delivery text. The proliferation of BYOD has paced this once consumer-focused smishing scam into the domain of businesses. A successful smishing attack on a personal device connected to the corporate website could result in a malware infection. Also, scammers are creating verified WhatsApp business accounts, and then using these to carry out delivery smishing scams: if the scammers spoof your business brand, your reputation may be damaged.
#2: Bank Alert Smishing
Bank alert scams are made to look like text messages from banks. In the corporate world, this could be a targeted smishing attack focusing on employees in the finance or accounts payable department. The smishing text would contain a link to a spoof but realistic-looking bank login page. The attackers would endeavor to collect personal or financial information and login credentials.
#3: Investment Scam Smishing
Investment scam smishing is on the rise. These malicious text or messaging app messages appear authentic and may look like they are from legitimate government agencies or known investment companies. Targeted smishing messages are generated based on collated intelligence on the target organization and will be especially difficult to identify as malicious. Investment scam smishing messages are typically geared up to steal financial information; a link to a spoof but realistic-looking financial website is often included in the message. As with the bank alert scam, the messages may spoof a known brand. Financial sector companies could risk brand hijacking and reputation damage if their brand is spoofed.
#4: CEO Smishing / CEO Fraud
Trust and the urge to do a good job are behind the act of CEO fraud or "CEO smishing". An example of the type of CEO smishing being carried out has been highlighted by the Better Business Bureau (BBB). The BBB gift points out that card scammers are targeting businesses. The targeted employee receives a text claiming to be from their boss; the scammers have previously collected intelligence on the company and target employee. The text contains the recipient's name, workplace, and boss's name. The message will say that the boss is stuck in a meeting but needs the employee to do a quick job for them. If the employee replies, they will receive a second text asking them to purchase gift cards for a client or wire funds to another "business", aka, the attacker's bank account.
CEO smishing is a tactic increasingly used in Business Email Compromise (BEC) scams. The smishing attack is initiated with an SMS text targeted at a specific employee, often working in accounts payable. The text received looks to be from the company CEO. The message will use social engineering, company branding, etc., and will to encourage the employee to send money to a fake client or similar.
#5: Technical Support Smishing
Smishing campaigns often look to steal login credentials that are then used to carry out further cyberattacks, like ransomware infections or data breaches. Text messages that look like they have come from technical support are effective ways to steal login credentials. The text messages contain urgent requests like "Your account has been compromised. Please click this link to enter your password, then reset to a new password within the next 20 minutes, or your account will be closed". An unsuspecting employee may click the link, which will take them to a spoof but realistic site they are used to visiting, like Microsoft 365. If they enter their login credentials as requested, they will be sent to the cybercriminal behind the smishing campaign.
#6: Calander Event Smishing
Scammers use events like tax season and holidays to trick targets into believing an SMS text message is legitimate. According to the 2024 McAfee Tax Scam Study, 1 in 4 Americans have lost, on average, $8,199 to tax scams. This figure covers victims of both online and text message phishing scams. Businesses are also at risk of tax fraud via SMS text, with IRS tax refund scams potentially targeting small businesses.
#7: Road Toll Smishing
In 2024, the FBI Internet Crime Complaint Center (IC3) received more than 60,000 complaints concerning road toll collection service smishing messages. The attackers appeared to be moving through each state.
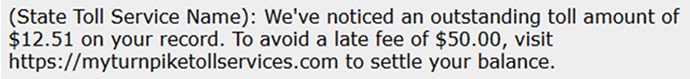
Source: FBI IC3 road toll smishing message
In a recent update, the FBI continues to warn about these road toll smishing attacks. The messages appear to look like local toll services like Fastrak. Organizations spoofed by a smishing attacker will suffer reputational damage.
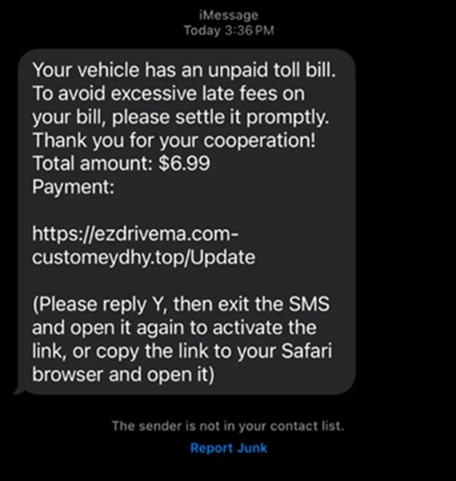
Source: IC3 interview with NexStar
How To Spot a Smishing Message

Spotting the signs that a text or messaging app message is fake can be tricky, especially if the message targets a specific individual. Smishing messages are also more difficult to identify than email phishing; the mobile interface makes it hard to identify the origin of a message. However, the following signs are typical of smishing messages:
- The message contains a sense of urgency or encourages panic.
- The number is not recognized.
- The message contains links – always be suspicious of links.
- The message requests personal or financial information.
- The message uses poor grammar or has spelling mistakes.
Two Large-Scale Smishing Attacks
Smishing is on the rise in business circles. Some of the most prominent smishing attacks include the following:
Bank of Ireland Smishing Attack
The Bank of Ireland suffered financial damage and reputation damage after a smishing attack affected 300 customers. The bank reimbursed the customers €800,000 ($840,000) after the customers were tricked by a smishing message into supplying bank details.
Twilio Smishing Attack
Twilio employees were targeted in a smishing attack that resulted in unauthorized access to customer accounts. The attack was described as a "sophisticated social engineering attack designed to steal employee credentials". The text messages spoofed the company's IT support, warning the targeted employees that their passwords had expired and they must urgently log in to change them.
What's the Difference: Smishing, Phishing, Vishing, and Quishing
- Smishing: uses mobile device messaging systems, like SMS text and WhatsApp to help carry out a cyberattack.
- Phishing: uses email to help carry out a cyberattack.
- Vishing: uses a conventional voice-based phone call to socially engineer a target as part of a broader cyberattack.
- Quishing: uses a QR code as part of a phishing or smishing attack. The QR code takes the victim to a malicious website.
Trends in Smishing
Use of Generative AI in smishing
Attackers are using generative AI to create all of the parts needed for a successful smishing campaign, including gathering information on targets, creating associate spoof webpages, and the content of the fake SMS text or messaging app message.
Overview of AbuseGPT Methodology

Source: sp24posters-final19.pdf
Security Workarounds
As security measures begin to impact the success of smishing, attackers circumvent protection by creating novel attack tactics. For example, an Apple iPhone workaround to auto-disable links in text messages is circumvented by encouraging the victim to reply using a y in the message. If they do so, the disabled links are reactivated.
"Mishing"
Cybercriminals are coordinating the features of a mobile device to help in the successful exploitation of individuals. For example, hijacking mobile device cameras. This mash-up of mobile attacks is known as "mishing".
Rich Communication Services (RCS)
RCS is the next generation of SMS technology. It incorporates richer text messaging features like CS-rich media, which could make smishing more prevalent as attackers can incorporate logos and other branding features. However, RCS could potentially help reduce the frequency of smishing by incorporating security features like sender information and digital signatures.
How To Prevent Smishing Attacks
The prevention of smishing is not dependent on a single measure. Instead, smishing, like phishing prevention, must be done using multiple layers of preventative measures, including the following:
Security Awareness To Include Smishing Simulations
Security awareness training educates employees and other business partners on phishing, social engineering, and other security risks. The training packages must also include specific training on the dangers of smishing. Some advanced awareness training platforms now include smishing simulations to help employees identify smishing attacks.
Be Aware that Smishing Attackers Can Easily Fake a Brand
Brand spoofing is a common tactic used in smishing attacks to exploit trust. All employees must be suspicious of messages that look like popular brands like Microsoft 365 or a bank.
Do Not Reply To the Message
Avoid replying to text or messaging app messages that are not verified.
Avoid Clicking Links in Text Messages or Messaging Apps
Avoid clicking links in any text or messaging app messages that are not verified.
Use Cross-Checks
Organizations must put cross-checks in place to avoid smishing. For example, any text or messaging app messages that purport to be from a bank asking for any personal or financial information must be cross-checked with your line manager of the finance department.
Enforce Multi-Factor Authentication (MFA)
If a malicious link is clicked and passwords are potentially exposed, using MFA on all accounts could help mitigate account compromise.
Use anti-malware protection on all device
An infected spoof website could cause a malware or ransomware infection. Deploy anti-malware software across all devices in your organization.
Report to relevant authorities
Always report a smishing attack to the relevant authorities, such as the FTC in the USA and the NCSC in the UK.
Block the Number
Block the number after identifying the message is smishing and reporting. However, remain vigilant as cybercriminals will use a new number.
Table of Contents
- What is Smishing?
- The Definition of Smishing
- What is Smishing?
- What Happens if Your Business is a Victim of a Smishing Attack?
- The Cost of Smishing
- Why Does Smishing Work?
- Seven Common Types of Smishing Attacks
- How to Spot a Smishing Message
- Two Large-Scale Smishing Attacks
- What’s the Difference: Smishing, Phishing, Vishing, and Quishing
- Trends in Smishing
- How To Prevent Smishing Attacks